KeePass 2.35 is the next version of the popular password manager that will introduce a new version of the KDBX file format and security improvements among other things.
KDBX is the file format that KeePass uses for information storage on the device. Version 4 of KDBX features improvements and new capabilities.
KeePass will use the new format eventually, but at first only if certain requirements are met. This is done to give ports of KeePass time to update their versions of the software to support the new format.
Basically, none of the following conditions need to be true:
- KeePass uses a different key derivation function than AES-KDF (the default and only used in KDBX 3.1).
- Plugins request to store custom header data in the KDBX file.
- Plugins request to store custom data in an entry or a group.
If none of the conditions are met, KeePass 2.35 will use the new file format automatically.
KeePass 2.35 and its security improvements
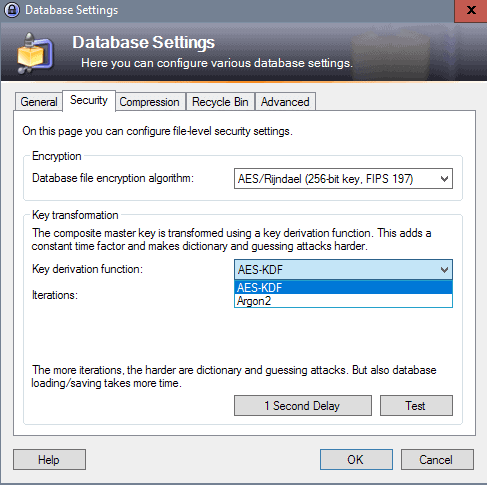
Probably the biggest change from a security point of view is support for the key derivation function Argon2.
The algorithm won the Password Hashing Competition against 23 candidates. Starting with KeePass 2.35 users of the software can switch the key derivation function from AES-KDF to Argon.
- Open KeePass 2.35 or later.
- Select File > Database Settings.
- Switch to the Security tab.
- Locate “key derivation function” on the screen. You may switch to Argon2 (and back to AES-KDF) with a click on the menu.

Once you have selected Argon2 as the key derivation function, additional parameters become available. You may change the number of iterations, memory, and parallelism.
You may increase iterations and memory to make dictionary and brute force attacks harder, but database loading and saving may take more time.
You may use the “test” button to test new values that you enter. KeePass runs tests and displays the time it takes to transform a key in a small window afterwards.

Some examples on a device with an Intel Core i7-6700k CPU and 32 Gigabytes of ram.
- Iterations 2, Memory 1, Parallelism 2: 0.003 seconds
- Iterations 2, Memory 250, Parallelism 2: 2.97 seconds
- Iterations 10, Memory 2000, Parallelism 2: 25.257 seconds
- Iterations 10, Memory 2000, Parallelism 4: 15.601 seconds
The main advantage of Argon2 over AES-KDF is that it provides better resistance against GPI/ASIC cracking attacks.
KeePass’ Argon2 implementation supports all parameters that are defined in the official specification, but only the number of iterations, the memory size and the degree of parallelism can be configured by the user in the database settings dialog. For the other parameters, KeePass chooses reasonable defaults: a 256-bit salt is generated by a CSPRNG each time a database is saved, the tag length is 256 bits, no secret key or associated data. All versions of Argon2d (1.0 to 1.3) are supported; KeePass uses the latest version 1.3 by default.
Other KeePass KDBX 4.x changes
Besides support for Argon2, KDBX 4.x will introduce a number of improvements and changes that are outlined briefly below:
- Improved header authentication — KDBX 4 uses HMAC-SHA-256 instead of SHA-256 for header authentication. This offers various advantages, one being that KeePass may verify the header before decrypting the remaining data.
- Improved data authentication — Similarly, KDBX 4 uses HMAC-SHA-256 instead of SHA-256 for data block authentication which is considered to be more secure and allows KeePass to verify the authenticity of a data block before trying to decrypt it.
- Plugins may extend the KDBX 4 header , may add other key derivation functions to KeePass 2.35 and later, and may store custom data in entries and groups.
- The ChaCha20 encryption algorithm is supported with 256-bit key and 96-bit nonce.
- Inner Header improvements that reduce the database size and improve loading and saving performance.
Additional information on the new format are available on the KeePass website. It is not clear yet when the KeePass 2.35 will be released.
Now You: What’s your take on the improvements?