The United States Computer Emergency Readiness Team (US-CERT) published a vulnerability note yesterday about a new zero-day vulnerability affecting Microsoft Windows 8, 10 and Server editions.
It reads:
Microsoft Windows contains a memory corruption bug in the handling of SMB traffic, which may allow a remote, unauthenticated attacker to cause a denial of service or potentially execute arbitrary code on a vulnerable system.
Attackers may cause a denial of service attack against affected versions of Windows by causing Windows devices to connect to a malicious SMB share. US-CERT notes that the possibility exists that the vulnerability may be exploited to execute arbitrary code with Windows kernel privileges.
Attacked systems may throw a blue-screen on successful attacks.
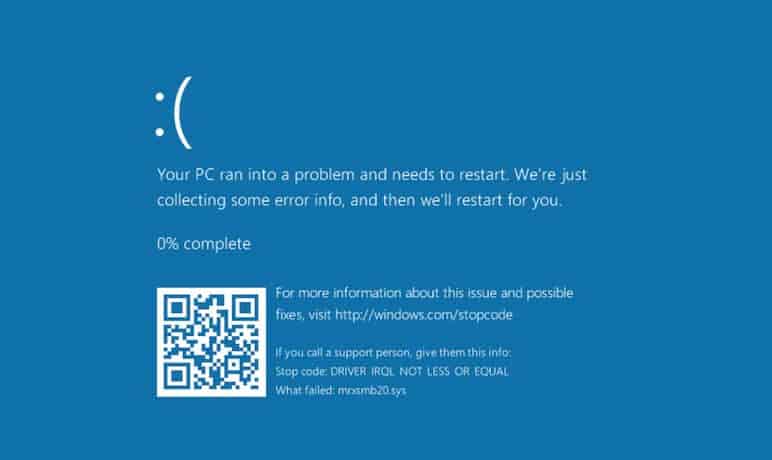
The vulnerability description offers additional information:
Microsoft Windows fails to properly handle traffic from a malicious server. In particular, Windows fails to properly handle a server response that contains too many bytes following the structure defined in the SMB2 TREE_CONNECT Response structure. By connecting to a malicious SMB server, a vulnerable Windows client system may crash (BSOD) in mrxsmb20.sys. It is not clear at this point whether this vulnerability may be exploitable beyond a denial-of-service attack. We have confirmed the crash with fully-patched Windows 10 and Windows 8.1 client systems.
US-CERT confirmed the vulnerability on fully-patched Windows 8.1 and Windows 10 client systems. Bleeping Computer notes that security researcher PythonResponder claimed that it affects Windows Server 2012 and 2016 as well.
While there is no official confirmation of that yet, it seems likely that the Server products are also affected by the vulnerability.
Severity and suggested workarounds
US-CERT classifies the vulnerability with the highest severity rating of 10 using the Common Vulnerability Scoring System (CVSS). Factors that play a role in determining the severity of a vulnerability include whether it is remotely exploitable, and how much expertise attackers require to successfully exploit the vulnerability.
Microsoft has not released a security advisory yet, but it is probably only a matter of time before the company publishes a security advisory to inform customers about the vulnerability and mitigation options.
US-CERT recommends to block outbound SMB connections on TCP port 139 and 445, and UDP ports 137 and 138 from the local network to the WAN. to protect Windows devices.
Home user networks may be affected by the vulnerability, but WANs are not that widely used in home environments.
To find out whether your version of Windows has any SMB connections, do the following:
- Tap on the Windows-key, type Powershell, hold down the Ctrl and Shift keys, and hit the Enter-Key.
- Confirm the UAC prompt that appears.
- Run the command Get-SmbConnection.
We will update the article once Microsoft publishes a security advisory for the vulnerability. (via Born City)