by Martin Brinkmann on November 04, 2018 in Security – 7 comments
A team of Stanford and UC San Diego researchers published the research paper Browser history re:visited recently in which four new, and working, browsing history sniffing attacks are revealed to the public.
Attacks that attempt to find out which sites a user visited are not anything new. Mozilla, for example, plugged a leak in 2010 that allowed site owners to use CSS to check a list of sites against a user’s browsing history using CSS.
The researchers found attacks that date back to 2002 using the :visited selector to determine whether a user on the site visited a linked resource previously.
The leak attacks affect all modern browsers that don’t block the storing of the browsing history; in other words, Firefox, Chrome, Internet Explorer and Microsoft Edge are vulnerable while Tor Browser is not.
Most web browsers keep track of the visited resources by default; this is a convenience feature that is baked into the browser. Browsers may suggest these resources again when users type into the address bar and users may search visited sites in case they need to revisit them but can’t remember the exact URL anymore.
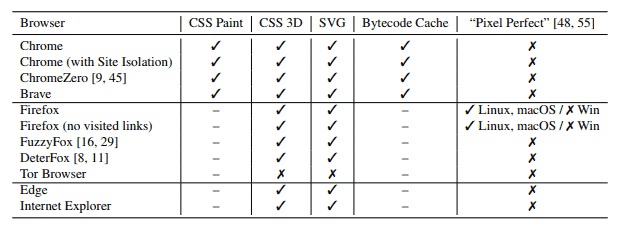
The first attack that the researchers discovered uses the CSS Paint API to determine whether a particular URL was visited by a user by “crafting a link element that gets re-painted only if its associated URL is visited” and monitoring timing information to determine if a re-paint event took place.
The second attack uses CSS 3D transforms, a technique introduced with CSS version 3. An attacker would stack 3D transforms on other CSS styles to create link elements and toggle “the link element between two different destination URLS” to identify re-paint operations.
The third attack uses SVG images and the CSS fill rule. The attack embeds a complex SVG image inside a link element and uses a “series of CSS fill rules under :visited selectors” to determine the visited status of a link.
The fourth and final attack uses Chrome’s bytecode cache to determine whether a JavaScript source file was loaded previously in the browser as these files are shared between pages of different origins.
All four attacks have in common that they need to specify URLs to check; none manages to retrieve a user’s entire browsing history.
How effective are these attacks? The researchers state that one of the attacks can determine the state of 6000 URLs per second; enough to check the most popular sites against the browsing history.
The researchers reported the issues to browser developers but patches for these attacks may take months to implement.
You can read or download the research paper in PDF format here.