by Martin Brinkmann on February 20, 2019 in Security – 3 comments
What would the result be if you analyze how popular password managers protect sensitive information such as the master password or stored passwords; that’s what Independent Security Evaluators tried to find out in their analysis of five popular password managers running on Microsoft’s Windows 10 platform.
The paper Password Managers: Under the Hood of Secrets Management looked at how the password managers 1Password, Dashlane, KeePass and LastPass handle secrets, and if it is possible to retrieve sensitive information.
The researchers analyzed the three states “not running”, “unlocked state”, and “locked state”. Main conclusions were that all password managers protected data just fine in not running state.
Not running refers specifically to a session in which the installed password manager was not launched or terminated by the user after launch.
Locked state describes a state in which the master password has not been entered yet or in which the password manager was locked by the user or automatically.
The researchers discovered that all password managers leaked data in unlocked and locked state under certain circumstances. The password managers 1Password and LastPass leaked the Master Password in unlocked and locked state, Dashlane all stored records, and KeePass passwords and other sensitive information the user interacted with.
The researchers noted that all password managers were susceptible to keylogging or clipboard sniffing attacks.
How severe are the issues?
The discovered issues in the password managers sound very severe on first glance. The leaking of sensitive data is certainly an issue and some companies could certainly do better when it comes to that.
Good news is that the attacks require local access or access to a a compromised system to exploit the issue. It is additionally necessary to target the issue specifically which would only make sense for targeted attacks or if password usage increases to a point where it is lucrative enough to exploit the issue.
In the case of KeePass, the user would have to have interacted with password entries for them to be exposed in system memory.
The author of KeePass noted some time ago that the Windows operating system may create copies in memory that KeePass has no control over.
Windows and .NET may make copies of the data (in the process memory) that cannot be erased by KeePass.
Protection
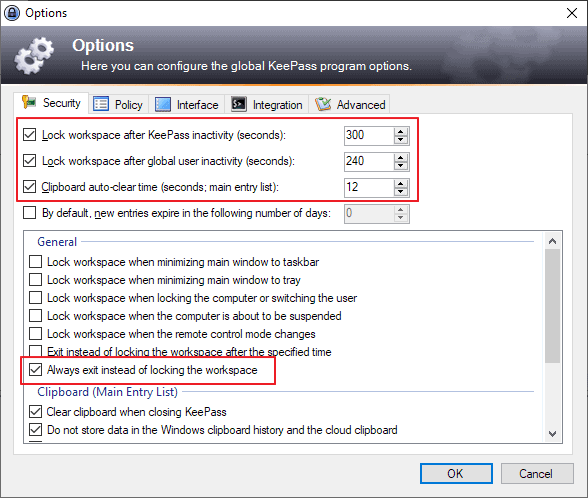
KeePass users can furthermore protect their data against attacks by making changes to the application’s preferences.
- Go to Tools > Options > Security.
- Check “Lock workspace after KeePass inactivity” and set it to the desired period, e.g. 300 seconds.
- Check “Lock workspace after global user inactivity (seconds)”, and set it to a desired period, e.g. 300 seconds.
- Make sure “Clipboard auto-clear time (seconds, main entry list)” is checked.
- Check the “Always exit instead of locking the workspace” option. The option terminates KeePass instead of locking it.
These settings close KeePass automatically on inactivity and protect all data from unauthorized memory snooping. The downside to that is that you need to restart the program when you require it again.
Check out my guide on improving KeePass security here.
KeePass users could also consider running KeePass in a sandbox, e.g. using Sandboxie, or virtual environment.
I don’t use the other password managers and cannot say whether they offer similar functionality.
Now You: Which password manager do you use?