![]()
Charlie Osborne
| July 23, 2021 — 12:33 GMT (13:33 BST)
| Topic: Security
Kaseya, an IT solutions developer for MSPs and enterprise clients, announced that it had become the victim of a cyberattack on July 2, over the American Independence Day weekend.
Who is responsible?
Charlie Osborne | ZDNet
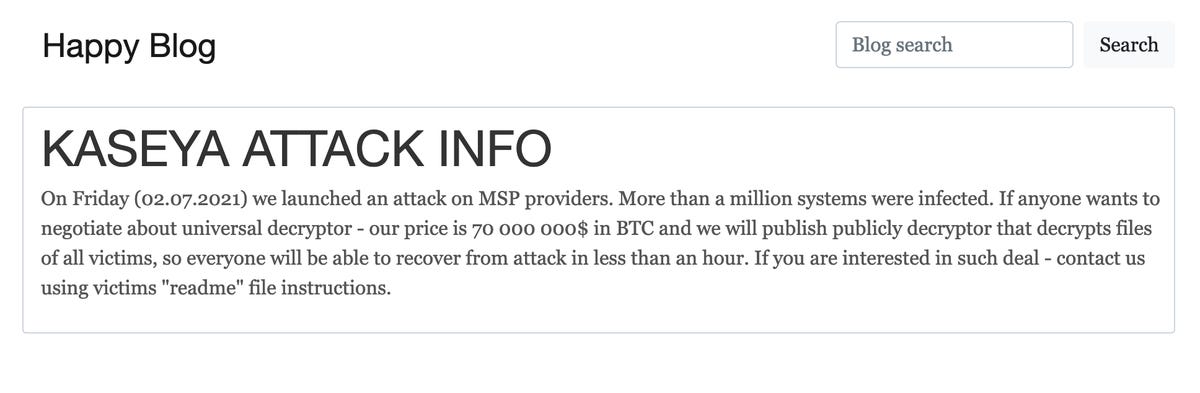
The cyberattack has been attributed to the REvil/Sodinikibi ransomware group, which has claimed responsibility on its Dark Web leak site, “Happy Blog.”
In an update over the weekend, the operators, believed to have ties to Russia, claimed that more than “a million” systems have been infected.
REvil has offered a decryption key, allegedly universal and, therefore, able to unlock all encrypted systems, for the ‘bargain’ price of $70 million in the bitcoin (BTC) cryptocurrency.
REvil has been previously linked to ransomware attacks against companies, including JBS, Travelex, and Acer.
What are the ransomware payment terms?
The ransomware note claims that files are “encrypted, and currently unavailable.” A file extension .csruj has reportedly been used. Operators are demanding payment in return for a decryption key and one ‘freebie’ file decryption is also on the table to prove the decryption key works.
The operators add (spelling unchanged):
“Its just a business. We absolutely do not care about you and your deals, except getting benefits. If we do not do our work and liabilities – nobody will not cooperate with us. Its not in our interests. If you will not cooperate with our service –for us, its does not matter. But you will lose your time and data, cause just we have the private key. In practice – time is much more valuable than money.”
Sophos malware analyst Mark Loman shared a screenshot on Twitter of a ransomware note planted on an infected endpoint demanding $44,999.
John Hammond, senior security researcher at Huntress, told ZDNet that the company has already seen ransom demands of up to $5 million.
Kevin Beaumont says that, unfortunately, he has observed victims “sadly negotiating” with the ransomware’s operators.
Fabian Wosar, CTO of Emsisoft, has also explained in a Twitter thread why using a key obtained by a single organization paying up is unlikely to be a viable path for unlocking all victims.
“REvil absolutely has the capability of decrypting only a single victim without these purchased decryption tools being applicable for other victims hit by the same campaign public key,” the security expert noted.
CNBC reports that the universal ransom demand has been reduced to $50 million in private conversations. However, as of July 7, the public demand for $70 million on the threat group’s leak site remains unchanged.
What are the reactions so far?
At the time of the breach, Kaseya notified law enforcement and cybersecurity agencies, including the Federal Bureau of Investigation (FBI) and US Cybersecurity and Infrastructure Security Agency (CISA).
The FBI and CISA have released a joint statement on the security incident and are urging customers to run a tool provided by Kaseya to determine the risk of exploit, and to both enable and enforce multi-factor authentication (MFA) on enterprise accounts, wherever possible.
Kaseya has been holding meetings with the FBI and CISA “to discuss systems and network hardening requirements prior to service restoration for both SaaS and on-premises customers.”
The White House is asking organizations to inform the Internet Crime Complaint Center (IC3) if they suspect they have been compromised.
On Saturday, US President Biden said he has directed federal intelligence agencies to investigate.
“Targeting [an] MSP platform (that is managing many customers at once) was very well thought and planned,” Amit Bareket, CEO of Perimeter 81, told ZDNet. “What’s unique is that hackers are becoming more strategic and targeting platforms that will filtrate down to many companies with one shot. RMMs [remote monitoring and management] are basically keys to many many companies, which amount to the kingdom for bad actors.”
The White House has attempted to strengthen its stance on cybercrime in light of this attack, warning Russian President Vladimir Putin that unless he deals with the problem in his own backyard, “we will take action or reserve the right to take action on our own.”
Are there any recovery plans?
As of July 4, Kaseya says the company has now moved on from a root cause analysis of the attack to recovery and patch plans, consisting of:
Communication of our phased recovery plan with SaaS first followed by on-premises customers. Kaseya will be publishing a summary of the attack and what we have done to mitigate it. Some lightly-used legacy VSA functionality will be removed as part of this release out of an abundance of caution. A specific list of the functionality and its impact on VSA capabilities will be outlined in the release notes. There will be new security measures implemented including enhanced security monitoring of our SaaS servers by FireEye and enablement of enhanced WAF capabilities. We have successfully completed an external Vulnerability Scan, checked our SaaS Databases for Indicators of Compromise, and have had external security experts review our code to ensure a successful service restart.
Data centers starting with the EU will be restored, followed by the UK, APAC, and then North American systems.
By late evening on July 5, Kaseya said a patch has been developed and it is the firm’s intention to bring back VSA with “staged functionality” to hasten the process. The company explained:
The first release will prevent access to functionality used by a very small fraction of our user base, including: Classic Ticketing Classic Remote Control (not LiveConnect). User Portal
Kaseya has now published an updated timeline for its restoration efforts, starting with the relaunch of SaaS servers, now set for July 6, 4:00 PM EDT and 7:00 PM EDT. Configuration changes to improve security will follow, including an on-premise patch, expected to land in 24 hours, or less, from the time SaaS servers come back online.
“We are focused on shrinking this time frame to the minimal possible — but if there are any issues found during the spin-up of SaaS, we want to fix them before bringing our on-premises customers up,” the firm says.
Additional security improvements include the creation of 24/7 SOCs for VSA, as well as a complimentary CDN with a web application firewall (WAF) for every VSA.
Update July 7: The timeline has not been met. Kaseya said that “an issue was discovered that has blocked the release” of the VSA SaaS rollout.
“We apologize for the delay and R&D and operations are continuing to work around the clock to resolve this issue and restore service,” Kaseya commented.
In a service update, the vendor said it has been unable to resolve the problem.
“The R&D and operations teams worked through the night and will continue to work until we have unblocked the release,” Kaseya added.
July 7, 12 pm EDT:
Kaseya hopes to resolve the SaaS systems rollout no later than the evening of Thursday, July 8. A playbook is currently being written up, due to be published today, which will provide guidelines for impacted businesses to deploy the upcoming on-prem VSA patch.
Current recovery status
As of July 8, Kaseya has published two run books, “VSA SaaS Startup Guide,” and “On Premises VSA Startup Readiness Guide,” to assist clients in preparing for a return to service and patch deployment.
Recovery, however, is taking longer than initially expected.
“We are in the process of resetting the timelines for VSA SaaS and VSA On-Premises deployment,” the company says. “We apologize for the delay and changes to the plans as we work through this fluid situation.”
In a second video message recorded by the firm’s CEO, Voccola said:
“The fact we had to take down VSA is very disappointing to me, it’s very disappointing to me personally. I feel like I’ve let this community down. I let my company down, our company let you down. [..] This is not BS, this is the reality.”
The new release time for VSA is Sunday, in the afternoon, Eastern Time, in order to also harden the software and bolster its security ahead of deployment.
July 12: Kaseya has now released a patch and is working with on-prem customers to deploy the security fix. Now, 100% of all SaaS customers are live, according to the company.
“Our support teams continue to work with VSA on-premises customers who have requested assistance with the patch,” Kaseya added.
What can customers do?
Kaseya has released a tool, including Indicators of Compromise (IoC), which can be downloaded via Box. There are two PowerShell scripts for use: one on a VSA server, and the other has been designed for endpoint scanning.
The self-assessment scripts should be used in offline mode. They were updated on July 5 to also scan for data encryption and REvil’s ransom note.
However, the scripts are only for potential exploit risk detection and are not security fixes. Kaseya will release patches as quickly as it can, but in the meantime, customers simply have to wait until Sunday.
Kaseya intends to bring customers back online on July 11, at 4 PM EDT.
“All on-premises VSA Servers should continue to remain offline until further instructions from Kaseya about when it is safe to restore operations,” the firm said. “A patch will be required to be installed prior to restarting the VSA.”
Cado Security has provided a GitHub repository for responders, including malware samples, IoCs, and Yara Rules.
Truesec CSIRT has also released a script on GitHub to identify and mitigate damage on infected systems.
Kaseya has also warned that scammers are trying to take advantage of the situation.
“Spammers are using the news about the Kaseya Incident to send out fake email notifications that appear to be Kaseya updates. These are phishing emails that may contain malicious links and/or attachments.
Do not click on any links or download any attachments claiming to be a Kaseya advisory.”
Are REvil still active?
After Biden made his stance clear to Putin on ransomware gangs, the REvil ransomware group’s leak site was seized and taken down by law enforcement.
The takedown included REvil’s payment site, public domain, helpdesk chat platform, and the negotiation portal.
While the intention was to secure some form of control over the group, it should be noted that ransomware operators often close down sites, rebrand, and regroup.
A side effect of the takedown is that the removal of negotiation and the possibility of purchasing a decryption key have left victims with unrecoverable systems. One victim who paid up for a decryption key — which ended up not working — is now out of pocket and unable to secure assistance from the cybercriminals.
A decryption key?
On July 22, Kaseya said that the company has managed to secure a decryption key. Obtained by a “third-party,” the decryption key has been tested successfully in victim environments — and the suggestion is that the decryption key may be universal.
The company is working with Emsisoft to reach customers still suffering due to locked systems and in need of a decryption key.
“We remain committed to ensuring the highest levels of safety for our customers and will continue to update here as more details become available,” Kaseya said. “Customers who have been impacted by the ransomware will be contacted by Kaseya representatives.”
Kaseya attack
Kaseya ransomware supply chain attack: What you need to know
1,500 companies affected, Kaseya confirms
US launches investigation as gang demands giant $70 million payment
Kaseya urges customers to immediately shut down VSA server
Related Topics:
Tech Industry
Security TV
Data Management
CXO
Data Centers
![]()
Charlie Osborne
| July 23, 2021 — 12:33 GMT (13:33 BST)
| Topic: Security