Cross-Domain requests describe requests from one domain to another. A typical example of this are Facebook information on another domain, to display a site’s followers for example or advertisement from third-party advertising companies.
But those example is obviously not malicious. There are two types of information that are traded that can be a problem for the Internet user. The first is privacy related. Information can be exchanged about your visit so that another entity receives information about that visit. This is usually used for advertising purposes to track a user on the Internet.
Considering that you reveal information as soon as you connect to a site or server, and that information includes your IP address, location in the world, operating system or language, it is fair to say that this is a privacy issue.
The second is more dangerous: malicious or undesired actions can be triggered by cross-domain request like Cross-Site Request Forgery attacks.
CSRF is considered very dangerous, as indicated by its ranking in the OWASP top 10 and the CWE/SANS top 25. The problem with a CSRF attack is that it makes requests on behalf of the user, without his/her knowledge. For instance, if a site (e.g. example.com) makes hidden requests to another site (e.g. myonlinebank.com), it can potentially cause harmful effects (transfer funds, create accounts, …).
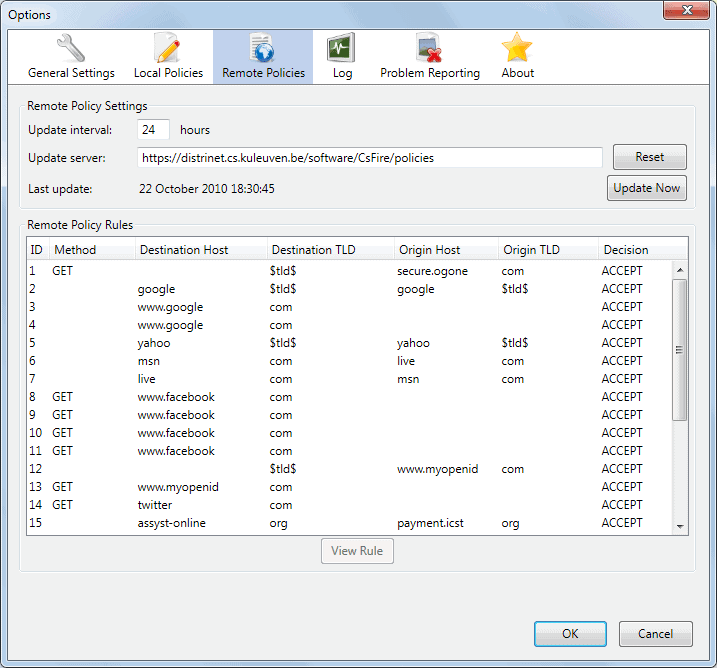
The Firefox add-on CsFire protects Internet users against malicious cross-domain requests. The add-on nullifies them by removing authentication information like cookies and authentication headers to eliminate the possibility that these requests can be harmful to the user.
CsFire provides a secure-by-default policy, which can be extended with fine-grained remote policies as well as fine-grained local policies. The remote policies are obtained from a policy server, to selectively allow certain harmless cross-domain requests (e.g. sharing items on facebook). The local policies allow you to specify certain cross-domain requests that should be treated differently, should you wish to do so (this is not required in normal surfing scenarios).
CsFire is based on an academic research paper CsFire: Transparent client-side mitigation of malicious cross-domain requests that was published on Engineering Secure Software and Systems 2010.
The CsFire add-on is available for all Firefox versions from Firefox 3.5 to the latest. It is possible to force compatible to make it compatible with the latest nightly builds as well.
Update: CsFire has not been updated since 2012 and it is unclear at this point in time if it still works in recent versions of the Firefox browser. While it is still possible to install the extension, it is unclear if all features work as advertised. Some that are visible do including the log file and the remote server update feature.
With that said, it appears that the add-on is abandoned and won’t receive updates anymore.